Create an account and login to use the Job Template to create a Job Label
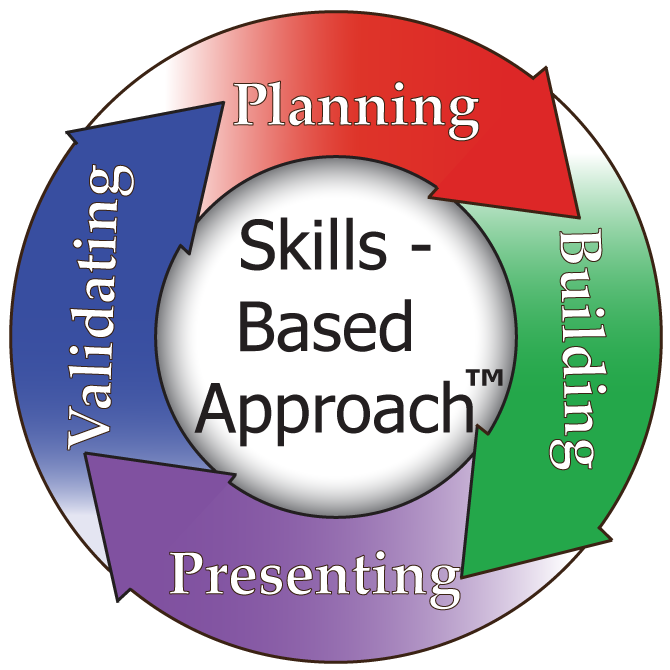
A Job Label is a complete ROI for a standard job listing lasting a year or less. Job Labels standardize what skills are required for both prior experience and first year application.
A template establishes baseline job requirements. A job posting and the company listing the job should have different requirements, so on a Job Label the referenced skills and their definitions change. Skills might get added or removed.
Use Job Labels to attract professionals. A clear advantage with Job Labels are they allow evaluations to consider not only a credential (degree or certificate), but whether workers are able to apply the necessary skills neeeded for the job.
Use the Learning Labels Search to find a Job Template. Then create a Job Label in seconds...
Use Skills Based Approach to prepare to learn, get, and verify the skills in 6 months to 2 years...